Best Practices for TikTok Research: Emerging Methods
| by Robin O'Luanaigh
With over 1 billion users worldwide, TikTok is an immensely influential social media platform, particularly among young social media users. Yet, despite its immense popularity and prevalence, there is a dearth published of best practices available to those interested in conducting research on TikTok. In this Research Note, Research Lead Robin O’Luanaigh draws on her experiences with the platform to provide a basic overview of current best practices for TikTok research and a baseline understanding of how the platform works. The Note starts with an overview of security concerns with the platform before moving to possible security measures researchers may wish to utilize. It then discusses two potential TikTok research methodologies, network analysis and algorithmic analysis of the platform, concluding with an example of such methodologies at work.
Security Concerns with TikTok Research
TikTok remains a controversial platform in national security spaces given its Chinese origins and its alleged connections with the Chinese government. The extent of this relationship between TikTok and the Chinese government has not been made readily apparent. However, data security experts posit that the Chinese government may have undue access to TikTok user data, prompting many governments (including the United States, United Kingdom, Canada, and across the European Union) to ban the platform from official government devices.
Even without a relationship between TikTok and the Chinese government, it is still possible for governmental or private operatives to access the platform’s data by nefarious means, including hacking the platform’s data. While such operatives may also be able to access user information from other social media platforms, what makes the hacking of TikTok data more problematic is the extent of the data the platform collects – TikTok has been accused of “mass data collection,” the legality of which depends on the location of the user, as the EU and other European countries have much more stringent legal protections for consumers than the US. Thus, the risk is not only in the possibility of the platform being hacked, but also in the extent of the gathered data possibly available to hackers.
An additional security concern levied against TikTok is the platform’s alleged potential leveraging for psychological operations, particularly given the platform’s purported connections with the Chinese government. This concern emanates from the Chinese government and military having a known focus on psychological warfare and the work of experts in neurotechnology asserting that TikTok can influence user beliefs and attitudes. However, analysis from the Center for Strategic and International Studies (CSIS) asserts that concerns regarding the possibility of Chinese psychological operations on TikTok don’t “hold up to scrutiny,” as the personal information gathered by the platform is of no greater intelligence value than data gathered by similar social media platforms, and that to date no malware has been discovered on the app. Additionally, the aforementioned neurotechnology expert alludes that the ability to influence user opinions is not specific to TikTok but instead endemic to social media platforms more broadly.
Other claims that TikTok engages in practices such as the provision of malware on user devices have not been substantiated. However, it has been established that the platform monitors user clipboards, or content that the user copies and pastes on their device outside of the app. This practice does not differentiate TikTok from other social media platforms who also engage in clipboard monitoring, such as Reddit and LinkedIn.
Security Measures while Conducting TikTok Research
For researchers conducting analysis on specific on-platform users and user networks, a VPN is likely sufficient as it obscures the researcher’s IP address. Upon setting up your VPN, utilize an incognito or TOR browser to protect your search history and information from possible platform data gathering attempts.
While a VPN is easier to use, a virtual machine provides added protection against the platform’s security concerns. TikTok researchers who wish to utilize a virtual machine may download the platform’s desktop version onto their virtual machine as opposed to using the browser version of the platform. This may mitigate the possibility of the TikTok browser slowing their research process down. In my experience, even using the TikTok browser without a virtual machine can cause large slow downs to the research process, but virtual machines can be further slowed down by TikTok’s audiovisual content.
Consider Your Location
The platform’s algorithm is heavily influenced by the location of your IP address, and should be of primary consideration when conducting research, especially research on how the platform algorithmically curates content. For example, I primarily reside in Washington, DC, and the content curated by my personal TikTok algorithm contains specific references to DC-area events, businesses, restaurants, etc. However, when I travel to other parts of the US, the algorithmically-curated content shown on my personal account eventually begins to reflect my current location. Both VPNs and virtual machines can be helpful in addressing this consideration. Researchers using VPNs may standardize their VPN’s location over the course of their research process, or key the VPN to specific geographical areas that are relevant for a given research question. In either case, researchers should utilize a VPN that allows users to select the location of their IP address for these purposes. Researchers using virtual machines have their IP addresses inherently standardized, while also having the additional device security afforded by a virtual machine.
Getting Started with TikTok Research
Most researchers will want to create a TikTok profile for every new research project they undertake, as the platform’s algorithm tracks search queries and viewed content. Creating a new profile for each research project ensures that that data collection is not influenced by past research (or personal use) due to the platform algorithm’s attempts to show you content it believes you might be interested in based on those previous searches. TikTok requires users to sign up using either an email or a phone number and sends a verification code to the chosen method of communication. I prefer to utilize an email address generator such as Temp Mail, which allows users to see emails sent to the randomized address without needing to log in to an email provider. If a phone number is preferred, researchers should ensure that a new one is used for each account, and ideally a phone number associated with a Google voice account or similar service, rather than a personal number. These steps apply to any TikTok researcher, regardless of their research question.
Research Method 1: Network Analysis
Researchers interested in a particular TikTok user or network of users will have fewer steps to take during their research process than those interested in algorithmically curated content. If the researcher has already identified an initial account to review, they can search for that account’s username in the platform’s search feature. They may then wish to review who the account is following if possible (some users make whom they follow private). For example, I might be interested in doing research on TikTok networks associated with the cottagecore aesthetic. I have identified an account with the username “cottagecore22,” the profile of which (as seen in the platform web browser) is provided below.
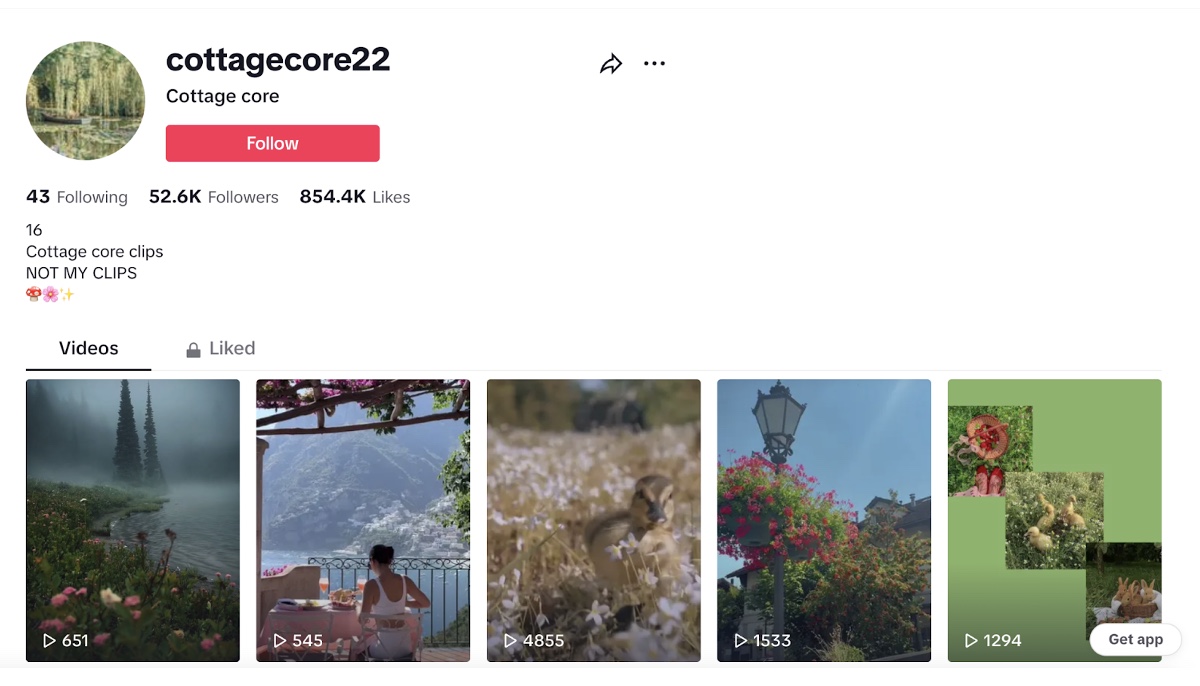
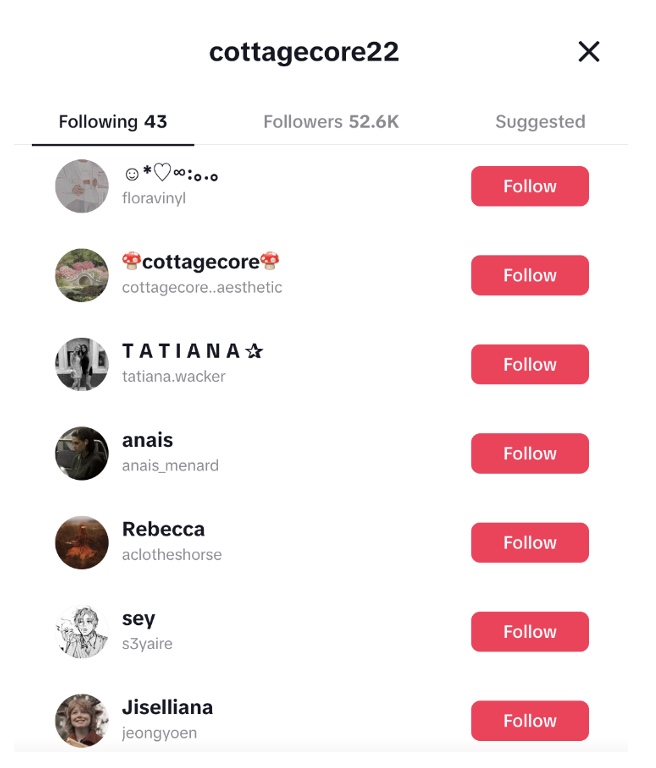
I may then wish to review the 43 users that this account follows. Thankfully, this user has not made their followers private, so if I click on “Following 43,” a pop up appears with the followed accounts. I can then review these accounts and begin to map out a network of cottagecore aesthetic enthusiasts on-platform.
Research Method 2: Algorithmic Analysis
Researchers interested in analyzing algorithmically-curated content will make significant use of the platform’s search query feature. Every TikTok account has a distinct, algorithmically-curated “For You Page” (FYP), which contains content selected by the platform algorithm. Initial content selection for the FYP is based on the data you provided during your sign-up process. As you utilize your account and engage with TikTok content, the algorithm curates your FYP based on your past on-platform activities. For example, if you have been searching for “dinner recipes,” the algorithm may begin sending you TikToks of baking recipes, which likely include recipes of initial interest but may then begin to encourage the viewer to increase their scope of interest, encouraging them to spend more time on the platform. Once again, it is imperative that researchers create a new profile and that they utilize an anonymous browser such as Incognito mode or TOR for each research task so that data collection is not influenced by past searches.
Algorithmic Analysis Example
The TikTok algorithm influences a variety of the platform’s features, many of which have not been appropriately studied. For the purposes of this Best Practices overview, I will walk through a short example of how algorithmic analysis can help researchers recreate a possible “average user experience” on platform to analyze the data subsequently collected from this experiment.
- Create a new TikTok account using a randomly generated email address and password. Open an anonymous browser and pull up the TikTok sign-in page.
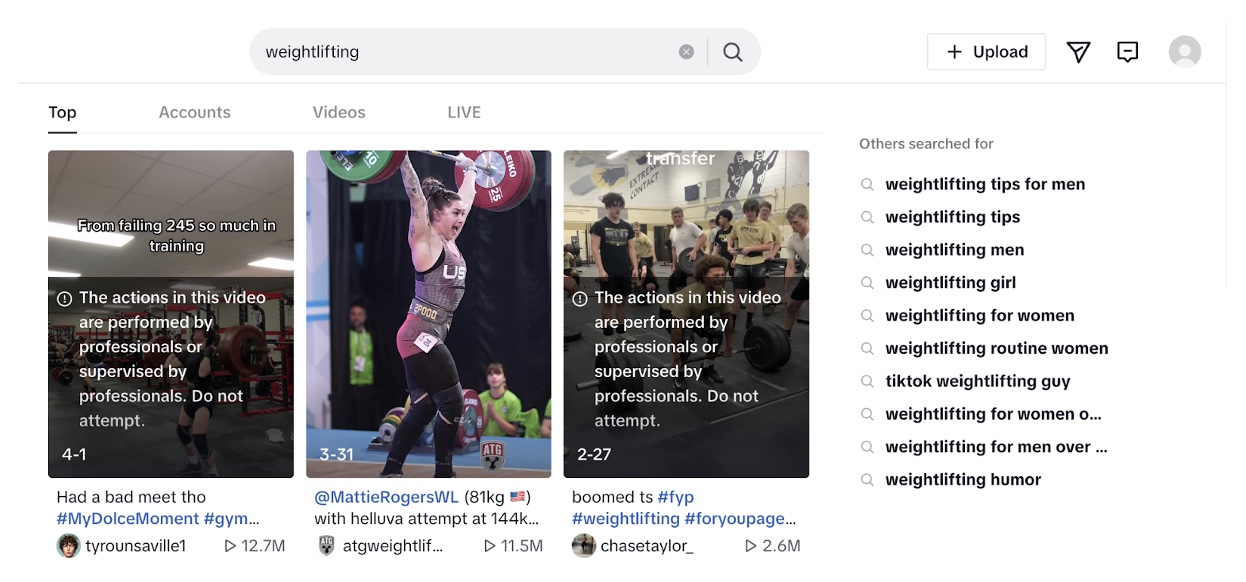
- Once logged in, use the search feature and type in a keyword related to a topic you wish to analyze. For this case, let’s say we wish to analyze algorithmically-curated content appearing in the search results of the query “weightlifting.” Below is a screenshot of the first three search results.
- When conducting algorithmic analysis, make liberal use of the “Top” category, as seen above. This category contains the most popular content that the platform associates with the keyword “weightlifting,” or whatever keyword you decide to use.
- Review the content within the “Top” feature, allowing you to analyze the most popular content associated with your chosen keyword without any algorithmic influence from past research or platform usage.
- If desired, a researcher may then wish to compare and contrast the content that appears in the “Top” category of different keywords, identifying overlapping trends, accounts, or hashtags, and thereby identifying on-platform connections between the two keywords.
Conclusion
Overall, TikTok remains an understudied yet immensely popular social media platform, and it is important to remember that best practices are always subject to change as the platform and its algorithm are likely to continue to evolve. As this occurs, and as awareness and understanding of the platform increases, it is likely that new research methodologies will arise. Armed with a baseline understanding of how the platform works, I look forward to an increase in researchers collecting and analyzing TikTok data.
